With the acquisition of Randori by IBM, clients’ use of attack surface management will be revolutionised
Today’s organisations must protect against a complex technology landscape that includes cyberattacks aimed at dynamic cloud, distributed, and on-premises environments. These modifications, which frequently evade security checks and recurring evaluations, create windows of opportunity for attackers trying to get past defences.
Unknown risks have existed and will continue to exist, but a contemporary cybersecurity programme must now include a continuous process to automatically identify unknowns, prioritise them, and communicate their importance to teams. IBM’s intention to purchase Randori, a top provider of attack surface management and offensive cybersecurity, in order to assist clients in managing this situation by providing an attacker’s eye view of their most vulnerable points.
With the most recent acquisition of ReaQta to assist in automatically detecting and blocking threats at the endpoint and the introduction of QRadar XDR and MDR services powered by our elite team of X-Force experts, IBM Security has placed significant bets on the need for both best-in-class defensively and offensively security.
With security tools to assist clients of all sizes better see what attackers see, IBM Security is now placing a further wager that cybersecurity must go on the offensive to safeguard the cloud, before any harm is done.
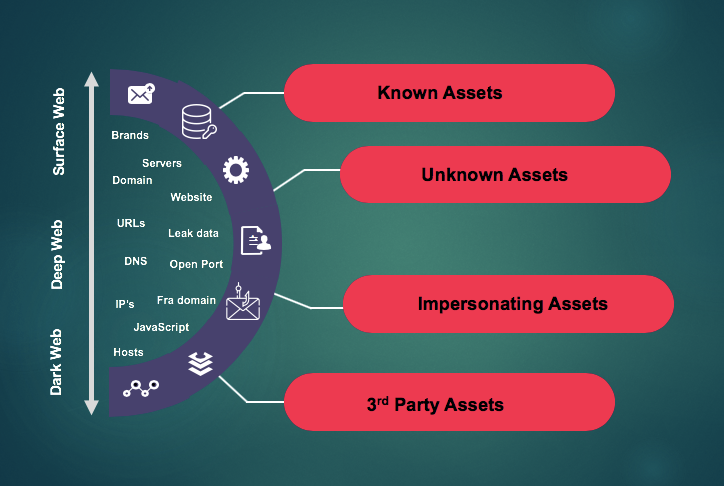
To understand your attack surface, an attacker is required. Despite further investment, investigations into recent breaches have revealed. Businesses still have trouble controlling their attack surface, or all the potential locations at which an unauthorised user could gain access to a system and extract data.
According to ESG, 69% of those questioned experienced a compromise in the previous year due to an unknown, unmanaged, or inadequately managed external-facing asset. Randori stands up in that situation.
A pioneer in attack surface management, Randori was developed by hackers with the goal of giving every organisation access to the attacker’s point of view. They accomplish this using an offensive security platform that mimics the strategies used by attackers to find and target large-scale enterprises for assault. Through recognising their most dangerous exposures, evaluating controls, and real-time defensive optimization, customers use this technology to stay one step ahead.



